Table of Contents
Introduction
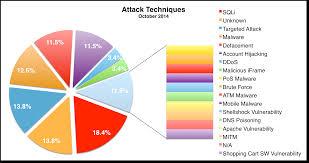
The internet has continued to revolutionize how various individuals communicate and interface with each other within the globe. As such, there has been a continued investment different computing infrastructure which has allowed institutions to perform their daily activities. Such computing infrastructure takes advantage of operating systems to run and have various applications installed that ensure that such tasks are performed. However, the integration of computing resources with the internet has opened up such resources to different cybersecurity vulnerabilities (Figure 2). There is a need for programmers to write better code that protects computers from cybersecurity threats.
Different programmers use different programming languages to develop software. The design of such languages can open up the software to different cybersecurity threats that may not necessarily be as a result of the code written by the developer. As such, there is a need for programmers to develop software with security in mind. If this is not done, then the society is opened up to cyber attacks (Schneider 36). By removing several insecure coding practices, then programmers can develop software optimized for cybersecurity.
Recommendation
Several practices should be implemented for better programming thus avoiding cybersecurity vulnerabilities. One of these practices is proper encoding. Programmers should always encode their outputs to protect them from any form of manipulation (Christey). Moreover, programmers should encrypt any data that is passed from clients to servers to ensure that the data is not accessed by hackers (Figure 1). Lastly, programmers should ensure that they set up clear access control structures within their software such that only the users allowed to access certain modules within the software do so. The above practices ensure that the programmers develop software that is secure.
Appendix
Figure 1: Android and iOS Applications cybersecurity threats
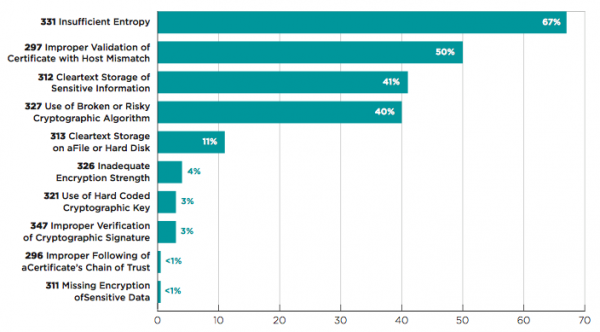

Figure 2: Attack techniques
- Christey, Steve “2011 CWE/SANS Top 25 Most Dangerous Software Errors.” CWE, 2011. < http://cwe.mitre.org/top25/ >
- Schneider, Fred B. “Impediments with Policy Interventions to Foster Cybersecurity.” ACM Vol 61, No. 3, 2018.

