Table of Contents
Introduction
Setting up an information infrastructure is the most vital part of any form of business whether large or small. Water Company is a large organization serving countries worldwide with stations based in South Africa, United States of America, and the United Kingdom. The IT infrastructure is set to begin from the city of Edinburg located in the state of Texas, Hidalgo County. Therefore a good foundation would be a plus in proper management of the company. IT infrastructure, therefore, refers to the complex hardware, network resources, software, and other services. The operation needs the above-described components, existence, and management of business IT environment. It permits the organization to convey IT services and solutions to its partners, employees, and customers. It is internally located within the firm, and its deployment is within the private facility.
The above-described components are vital in the setup of IT infrastructure. The breakdown of each requirement is thereby, highlighted as follows: Hardware consists of computers, servers, computers, data centers, hubs, routers, switches, etc. The Software part consists of customer relationship management, enterprise resource planning, productivity applications, etc. The network is composed of Internet connectivity, firewall, security, network enablement, etc. Lastly, meatware also known as liveware or wetware is a fundamental part of the IT infrastructure. It refers to elements of human beings in the environment of computer systems (Chandra et al. 2014). The personnel is essential in the running computer operations, and they entail developers, network administrators, designers, and generic end users having IT appliance accessibility.
Setting up an excellent ICT infrastructure has many importance and functionalities as described below: IT infrastructure gives a data movement protocol from one geographical location to another as fast as possible so that intended target can use it appropriately. The data movement consists of local movement, and that means the data transit to the server for a particular utilization or require alterations then it returns to the storage. Also, there is client/server data movement that allows users to access the intended information via their devices such as PC, smartphones, tablets, etc. The users pull the data from the primary location to their devices.
Additionally, IT infrastructure includes network cables, transmission media, antennas and satellites, aggregators, routers, repeaters, and any device involved in the path of transmissions. A good ICT infrastructure should give a suitable platform for the required IT apps and the necessary functionalities for the end users. In the viewpoint of IT infrastructure as the single entity, enables efficiencies and effectiveness as the resources optimization occurs for various workloads, and those alterations that may happen in the interrelated resources can be comprehended readily and solved as soon as possible. For example, IT manager can decide to increase the number of servers to solve constrained workloads in CPU.
Therefore, the project aims to come up with an authentic IT infrastructure for the Global Water Company so as to improve the effectiveness and efficiency of the company. The IT infrastructure to be made is also projected to take care of technological changes over time (Chandra et al. 2014). It helps in solving ever-changing customer needs.

Literature Review
The IT infrastructure must consist of information, services, and network system. The information refers to facts that are used within the organization to make critical decisions. The information procurement is evolutionary, and the accessibility of the data in the company can be summarized as indicated in the picture below.
Figure 1: Information Accessibility
(Smriti, n.d.).
There is also need to have the facilities that generate the information described above. The services must be dynamic to change with the ever-changing environment. The services should be capable of making information regularly. Therefore, the services would need resources commitment for maintenance and establishment. Another name for resources is data processing resources. Thirdly, the network is very crucial for the IT infrastructure. The descriptions of the components of the IT infrastructure are as follows:
Data Center
It is a facility that assists in the centralization of IT equipment and operations of an organization. It also centralizes where the firm stores, disseminates and manages data. Data center has vital systems that aid in daily activities. Therefore, its reliability and security are top priority for any organization whatsoever. Data center include servers, network equipment, computers, security such as biometric and firewall security systems, data center management software, and storage such as backup storage or storage area network (Geng, 2014). The non-computing infrastructures include physical server racks, cables, power devices, cooling devices, internet backbone, etc.
Historical Background states that data center originated from big computer rooms of ancient times around 1945 when army built a massive machine known as ENIAC. Later on in 1960 mainframe computers emerged and could only be used in government offices as each one could cost around $5 million. No one could afford the computers. They were too expensive, and its use involved exclusively military operations. Deployment of microcomputers began in the 1980s, and the manufacturers did not care much about OS. Need for IT resources thereby came into existence as operating systems Linux compatible computers featured in the 1990s. The name server, therefore, originated from then.
A company could use the hierarchical design of servers with the use of inexpensive of networking equipment. The adoption of data center gained popularity in 1997-2000 due to company’s need for fast internet connectivity. Companies began through the building of internet data centers to offer clients large system operations. New technological advancements then emerged towards private data center. Cloud data center appeared as well. Collectively they are currently referred to as data center.
Server
It is a program in a computer providing required services to other users on other computers or the same computer. The server also refers to the computer in which the server runs in. The server can either be utilized for other purposes, or it may be a dedicated server. Server consists of:
- Application server: It is a program that exists in a distributed computer network providing a business logic usable in application programs.
- Mail server: An app that gets arriving e-mail from the local users that are individuals in the same domain, and the remote senders. It then forwards outbound e-mail for conveyance.
- Virtual Server: A program that runs on the shared server. The shared server is configured in a manner to look like every user have a whole server control.
- File server: A computer that stores and manages data files. It is centrally located so that other computers on the same network can access the data.
- Proxy server: It is a software acting as an intermediary amid endpoint gadgets, and additional server whereby a client or user requests service.
- Blade server: It is server chassis that houses server blades (modular circuit boards). Each blade acts as a server on its capacity and is dedicated to one application.
- Policy server: It is a security component in a network system providing services of authorization. It also enables files’ control and tracking.
Network Services and Equipment
They include all the physical devices that are needed for the interaction and communication between the devices on the network. They function in the computer network to mediate data. They include routers, gateways, modems, network bridges, networking cables, wireless access points, line drivers, hubs, switches, repeaters, firewalls, multiplexers, protocol converters, etc. The services that are part of the data center would include source control systems, issue tracking systems, and wireless communication services (Great Britain, 2006).
Issue Tracking System
Issue tracking is a computer-based software. It maintains and manages the items list in a firm. It is typically used in the customer’s support center to generate, apprise, and resolve problems from customers. Therefore, the support ticket should offer relevant information on every client. It gives customers chance to report problems and be able to track the progress of his/her problem. Additionally, it offers an opportunity to realize the responsible person for problem solution. It also gives managers mandate to customize various procedures to give fast time solutions and eliminate time wastage. It is applicable in most companies and therefore, for improved customer’s relations in GW, it would offer a great deal.
Technological Evaluation
Technological evaluation of various infrastructures in the firm entail all the principles, techniques or tools, and methods utilized to do valid assessments on the potential values of different technology values. It improves company’s profitability and competitiveness. Therefore, thorough evaluations assess the IT infrastructure and various devices within the system’s network. It assists in screening new concepts, evaluating new technologies both noninnovative and innovative. In a simple definition, it entails new ideas examination, recognition and analysis of potential changes and causes, selecting and executing proposed technology, and plan and develop solutions to problems. Discussed here below are the primary technological evaluations of the Global Water IT infrastructure.
ICT Infrastructure Management and Administration
The assessment of the ICT administration and management would provide a review on how the current IT environment is managed. It would entail projects, staffing, plans, documentation related to policies and policies, and budgets. An evaluation in the company would involve assessment professional employees concerning necessity of the organization. Such need includes ability of practical skills.
Their capability on practical skills on IT infrastructure is vital for management criteria and administration of the IT infrastructure. Secondly, the communication assessment is also very essential. It enables to realize the communication capability among the administration so as to share any problem that may arise in the firm about IT problems (United Kingdom. Treasury. Office of Government Commerce, 2002). Thirdly, assessment of the management ensures thorough teamwork and fast decision making.
Survey
Conducting a study on the new IT infrastructure would be crucial. It will aid in realizing the problems that all the IT community may have. It involves conducting a survey of the customer’s based users and within the offices. The results provided will be a result of problems accompanied with recommendations on how to address any identified issue.
Backup environment
There are a big common problems to most IT infrastructure in the world. Taking an inventory of objectives of recovery time objectives of business objectives, existing backup environment, and the apps recovery point objectives is vital. It would save cost while maintaining the value of the organization’s goals. For example, dedupe on the disk can save the firm a large sum of cash. Furthermore, disk can still be leveraged.
Backup is the biggest headache facing most organizations. It is important for an IT department to take an inventory of the existing backup environment, business objectives for recovery time objectives (RTO) and recovery point objectives (RPO) for applications. In an optimized IT model, backup and recovery are typically the largest benefactors from a cost savings perspective. Dedupe to disk can save your organization a ton of money while still letting you leverage tape for long-term archives. Make sure the solution you choose integrates with any existing tape backup environment and enables you to automate tape for long-term archives after data is replicated offsite.
The evaluation of a proposed technology must be very careful, considering and identifying all the factors that will affect the whole organization. These main factors are expected financial benefits, competitiveness, added value in its products and the impact upon the business as a whole.
The present technique can either be applied in small, medium or world-class enterprises to evaluate mid and high tech technologies. Deduplication to the disk can save a lot in the organization as it allows disk storage for long time archives. The chosen solution must integrate with present tape backup criteria, and automation is in place for offsite archive after data replications.
Network Fixing
The system must be robust, both WAN and LAN. It will give high performance for all the client’s accessibility while ate the same moment offering lasting bandwidth for the movement of data amid the locations. The bandwidth for the WAN is very crucial for the replication of data and the Data Recovery (DR). Therefore it must be robust to give handle all the workload productions. At the same time, meets RPO (recovery point objectives) through maintenance of bandwidth that keeps data in sync (Chandra et al., 2014). Therefore, minimization and optimization of bandwidth are vital due to an expensive feature of the WAN. Solutions involve investments in methods that tend to replicate data while taking care of DR maximum efficiency and allows LAN-free, and sever-less backups to eliminate traffic from the network.
Servers and Apps Optimization
Virtualization of servers saves a lot in the reduction of cost since less hardware is used. In the case of Global Water (GW), Co. server hardware is a standard HP ProLiant ML350 G6 with 2 TB is used. It is cost efficient and offers consolidation of processes. Very fewer physical servers are needed at the remote sites.
SAN Virtualization
The SAN (storage virtualization network) can be very expensive in IT since it contributes to the operational expenditures. Therefore, all the measures must be taken accordingly to offer high performance, robust, and infrastructure reliability. Instead of buying monolithic storage arrays a firm can mirror data amid two lower modular arrays of storage. It helps in the accommodating disk so as maintain low cost. It also encourages honesty in the IT department.
Solution
Design
ICT infrastructure design for the Global Water is done for the countries namely, South Africa (SA), United Kingdom (UK), and South Africa (SA). The connection begins at Edinburg in the United Kingdom. The server at the Edinburg connects to the switch which is then linked to the servers in Durban South Africa and server in Birmingham US. In Edinburg, there are 700 desktops and are served directly from the server via the switch. They control the original information in the company and therefore, selectively allows information retrieval to other users. In South Africa, there are 400 desktops located in Durban, Cape Town, and Johannesburg. The server is placed at Durban and serves all the three towns. The users in each of the three location are 750. Lastly, US has 800 desktops located in Birmingham and 710 users. In New York, there are 750 users. The server is based in Birmingham.
The internet connectivity is through WLAN connection in every location. Each location has WLAN capability. The internet goes via router and firewalls then to the WLAN for accessibility in each of the sites. The use of modern technological advancements in the solution criteria aids in cost reduction and efficient communication between the locations.
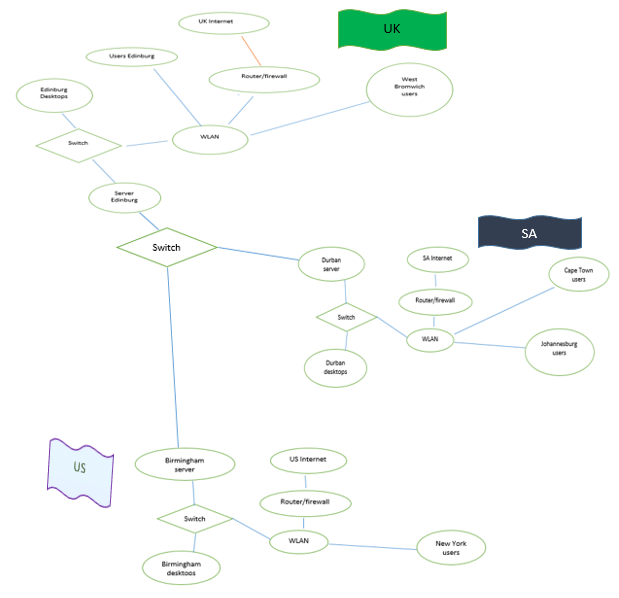
Figure 2: ICT Network Structure
Theory
The basic ICT infrastructure features are taken account of and described as below. The significant features that aid in the set-up of the infrastructure include servers, routers, firewalls, switches, WLAN, etc.
WLAN
It links two or more gadgets with the use of wireless distribution criteria. The wireless method is always OFDM or the spread spectrum within a specified range of area. It gives users the ability to relocate while accessing the internet. Its connection can be as broad as possible. Its use and installation are easy. Its invention is credited to Abramson Norman back in 1971, which he named ALOHAnet.
Firewall
It controls and monitors the inbound and outbound network traffics according to security rules. It induces a barrier between the secure, trusted and another unknown network such as recognized insecure network system. There are two types; network and host-based firewalls. Network firewalls filter amid two or more types of networks and they are hardware based and software based firewall. Firewalls have existed for over 25 years as a first defense line in the security systems of the networks. In summary, they generate a barrier between controlled, and secured that are trusted and the networks that are not trusted such as the internet (CISCO, n.d.).
Gant Chart
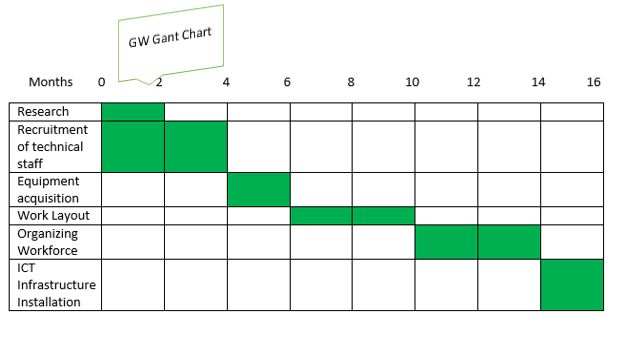
Figure 3: Gant Chart
Budget Plan
| ACTIVITIES | COST in $ |
| Research | 5k |
| Recruitment of technical staff | 5k |
| Equipment Acquisition | 10k |
| Organizing workforce | 5k |
| ICT infrastructure Installation | 20k |
| TOTAL | 45K |
Figure 4: Budget Plan
Conclusion
A good IT infrastructure is that having several importance and functions well. The most fundamental reason behind designing the best IT infrastructure is to reduce cost while improving the productivity. In the context of productivity, customers’ relations are put in place, and features such as issue tracking are a plus in improving customer’s experience. Therefore, the IT infrastructure should be done well to aid in the proper work within the firm. The protection should be thorough enough to take care of spyware and phishing attacks (Computer Society of India., & In Satapathy, 2014).
A brief insight into these threats includes Trojan horses, propagating worms, spyware, phishing, and any vulnerability. They can slow down the connectivity within the enterprise. Furthermore, they can result in a crash of the whole system. Therefore, to avoid such problems, an IT assessment must be done while placing thorough security to the entire system.
The distribution, acquisition, and management of the ICT resources are necessary. The needs of the organization are understood at this moment, and thus evaluations are done towards achievements of the goals. Therefore, an ICT infrastructure should be regularly assessed for various problems to improve firm’s productivity.
Abbreviations
- CPU – Central Processing Unit
- DR – Data Recovery
- GW – Global Water
- ICT – Information and Communication Technology
- LAN – Local Area Network
- RTO – Recovery Time Objectives
- SA – South Africa
- UK – United Kingdom
- US – United States
- WAN – Wide Area Network
- Chandra G., Michael H., and Kara S., 2014. Next-generation IT infrastructure. [Online]
- CISCO, n.d.. What is Firewall? [Online]
- Computer Society of India., & In Satapathy, S. C. 2014. ICT and critical infrastructure: Proceedings of the 48th Annual Convention of Computer Society of India.
- Geng, H. 2014. Data Center Handbook. Wiley.
- Great Britain. 2006. ICT infrastructure management. London: TSO.
- Smriti, C., n.d.. IT Infrastructure: 3 Basic Elements by which the IT Infrastructure is Built Up. [Online]
- United Kingdom. Treasury. Office of Government Commerce. 2002. Best practice for ICT infrastructure management. Norwich, UK: Stationery Office.
